The Internet has many levels, from the most obvious to the most hidden, because it is an extremely extensive worldwide system and contains information on everything (and practically everyone). Not all levels are created equal; some include more information than others.
The Internet is getting more advanced daily, both exciting and terrifying. When we come across stories and news concerning the Dark Web, it’s natural to feel apprehensive since there is so much we don’t distinguish and can’t control. This menacing moniker immediately conjures images of danger in our minds.
While some may prefer to use obfuscator language about the Dark Web to instill a sense of foreboding, this book will dispel any such notions by providing precise and concise information on the Dark Web, its operations, and the impact they have on your online safety.(1)
Distinguish Between The Dark And Deep Web?
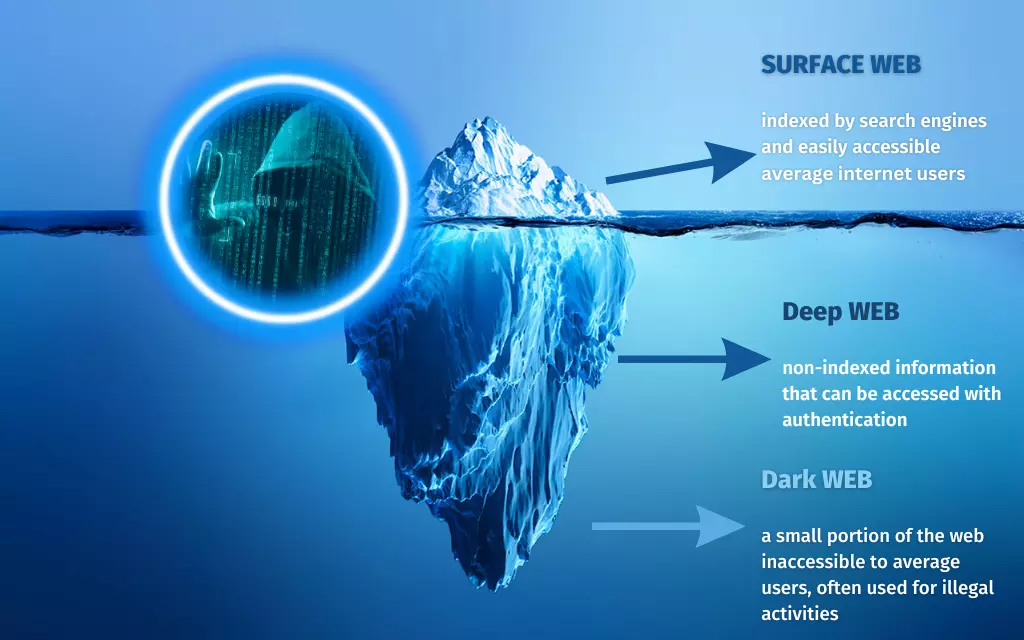
Despite the popularity of online search engines, the vast majority of the world’s digital material is still inaccessible to them.(2) The Deep Web, sometimes known as the “hidden web,” is home to this vast trove of data and is the primary location for most internet interactions.
You routinely incorporate Deep Web usage into your daily life. You are always on the Deep Web when you access your email, check your online banking, or browse social media. For security and privacy reasons, most content on the Deep Web is protected behind login credentials.
These are just a few examples of Deep Web entities:
- Databases
- Internet-based social networking software
- Financial transactions are performed through the Internet.
- Intranets
- Forums
- Content behind a paywall
Medical and legal records, bank statements, academic papers, trade secrets, and other private business information are only a few examples of data commonly exchanged on the Deep Web.
While you might not use the phrase “Deep Web” frequently or ever, it is more likely that you have encountered it than you know.
Though you may have heard of the Dark Web, this is not the same. In the same way that the Deep Web is distinct from the rest of the Internet, the Dark Web is also different. Let’s analyze the sources of its lousy rap to find out why people don’t like it.
What is Dark Web?
While the Dark Web’s beginnings are murky at best, it is now commonly acknowledged as the unsavory breeding ground for a wide range of cyber security threats.
Darknets are a collection of nodes and networks used on the Dark Web. Many different kinds of P2P networks are both operated and used by groups and individuals.
Users must install additional software, such as the Tor browser, to reach the Dark Web. It’s essential to understand how Tor operates and why it exists because it plays such a significant role in everyday online life.
Let’s Define the Tor Browser
The Tor Project, created in the mid-1990s to protect U.S. intelligence communications, is currently the most popular means of accessing Dark Web materials.
To protect its users’ anonymity online, the Onion Router (thus the name Tor) employs three distinct levels of encryption and a tailored method of rerouting web traffic. Using the Tor network of relays, it encrypts data at many levels and randomly sends it across the Internet.
The Dark Web employs stringent admission requirements to ensure that users’ identities, online pursuits, and physical whereabouts remain concealed. People can safely converse and share information on the Dark Web using the Tor browser without fear of revealing their true identities. Most people hide their identities even further when they’re on the Dark Web by connecting to a VPN.
Some people incorrectly refer to the Tor Project and Freenet as just another name for the Dark Web. The necessity for anonymity and security in online communication gave rise to the Tor network and comparable routing systems.
Those who rely on the Dark Web to carry out potentially harmful but not necessarily unlawful activities include:
- Whistleblowers
- Opposition figures in authoritarian governments
- Activists
- Reporters who have to keep their sources secret
- Justice system
- The Intelligence Community
As expected, criminals and other foolish people have figured out how to utilize this level of anonymity to conceal their identities, commit crimes, and elude authorities.
Why Is It Risky to Use the Dark Web?
Cybercriminals and other bad actors frequently utilize the Dark Web’s resources to further their illicit goals. When it comes to the underground economy, the Dark Web’s markets and forums are where it’s at.
Stolen and counterfeit data comes in numerous forms, and sellers and buyers frequent these illegal marketplaces to exchange them.
Details about an Individual’s Identity
Any information that may be used to identify a specific separate, such as a name, address, phone number, date of birth, Social Security number, compromised email address, etc. (Also known as PII or personally identifiable information).(3)
Facts And Figures about Money
Information includes stolen credit card numbers, user names and passwords for online banking, cryptocurrency account data, banking, and insurance records.
Information Needed To Access an Online Account
Accounts for anything from social networking to ridesharing and video streaming to paid professional services — including genetic testing and antivirus software — often require a username and password to gain access.
Relevant Health Information
Including but not limited to your medical history, medications, biometric data (such as fingerprints and photographs of your face), test results, billing information from medical institutions, and other sensitive details (also known as PHI, personal health information). This can cause problems like fingerprint identity theft and medical identity theft.
Proprietary Business Information
The scope of this classification extends to things like intellectual property, patents, competitive intelligence, and even internal business procedures.
Misleading Information
Most notably, forged travel documents, stolen photo identification documents, bank drafts, and other forms of counterfeit currency.
Black markets sell stolen information from not only data breaches and other forms of cyber assaults and online frauds but also narcotics, access to new forms of malware, and even assassins for hire.
Silk Road was the most well-known Dark Web bazaar, serving over 100,000 customers at its height. The website Ross Ulbricht launched in 2011 quickly became the go-to marketplace for illegal goods, particularly drugs. In 2013, the FBI shut down Silk Road. However, the site temporarily returned to its 2.0 iteration before being permanently shut down again by government enforcement.
Throughout the takedown operation and the following decade, the U.S. authorities seized almost $1 billion worth of bitcoin. Ross Ulbricht was given two life terms in addition to three additional convictions.
People visit Dark Web markets for various reasons, not the least of which is the prospect of generating substantial sums of money there. Plenty of child pornography may be found in this web area, with some sites attracting tens of thousands of visitors every month.
The Dark Web is more than a marketplace since it is also a center for other illegal activities. As a bonus, it provides services that hackers may use to launch assaults with minimal preparation and expertise.
Services Available to Cybercriminals on the Dark Web
Although it may seem priceless that fraudsters sell private information on the Dark Web’s underground markets for pennies.(4)
Information for credit cards with a maximum limit of $1,000 costs an average of $150, whereas data for an online banking account with a minimum amount of $100 sells for only $40.
Compare it to the $4 price of a compromised Uber rider account and the $48 value of a Netflix account with a paid annual membership. Expensive items that are difficult to get, such as a French passport, can reach upwards of $4,000.
To help customers determine which vendors to do business with, Dark Web marketplaces implement review and rating systems. These characteristics, along with the allure of cybercrime riches, explain why the Dark Web Price Index reports a dramatic increase in supply on these underground markets.
In addition to selling personal information and access to compromised accounts, hackers on the Dark Web also buy and sell the tools and resources necessary to conduct cyber assaults, espionage, and other forms of cybercrime. To infect systems and spread malware, fraudsters often turn to commercially available software exploits (exploit kits).
Malicious programs already installed and ready to steal data, steal identities, monitor user activity, and so on are known collectively as malware (with self-replicating capabilities). Malware-as-a-service is a subscription-based model that provides cyber criminals with the software and hardware they need to launch assaults, including malicious software, a distribution network, a selection of targets, technical assistance, and a dashboard from which to monitor and control the operation.
Defects in software that even the developer doesn’t know about (called zero days). That’s a tool cybercriminals may use to get into businesses undetected. To gain entry to botnets or networks of hacked devices, malevolent hackers use to get access to the computational resources necessary to launch attacks.
DDoS services use the resources of large botnets to overwhelm their targets with traffic and bring down their servers and the services they provide. Tutorials, manuals, and other information that help cybercriminals become more proficient in their chosen fields are all considered part of cybercriminal training. Swindlers can use money laundering (money mulling) to conceal the origins of the funds they steal, extort, or otherwise get from their victims.
This package’s high quality and inexpensive cost have drastically reduced the entrance cost. Still more worrying is the fact that hackers have figured out how to make a lot of money off of people and businesses all around the world quickly and on a large scale. Because of the anonymizing features of the Dark Web and cryptocurrency transactions, this area has become fertile ground for criminal activity of all stripes.
There is a reasonable risk that part of your information has leaked in a private data leak on the Dark Web, which is home to several unlawful websites, forums, blogs, and data repositories.(5)
Law and Dark Web
Dark Web access is not prohibited, despite the ominous term. However, it is an irrefutable reality that most Dark Web activity is connected to illegal activities.
When Using the Dark Web, What Risks Should You Be Aware Of?
Suppose you are found purchasing an illegal firearm or narcotics or stumble upon a child pornography website while exploring the Dark Web. In that case, you might face severe legal penalties, including loss of freedom.
Unlike the World Wide Web, which has security features like your browser’s built-in protection against rogue websites, this segment of the Internet does not. Chrome and Firefox, for instance, both provide security notifications when you attempt to visit phishing websites. The Tor browser prevents this from occurring.
The Dark Web is rife with malicious code like malware, ransomware, and trojan horses. Unless you have a specially designed cybersecurity setup, you risk infecting your devices.
Swindling People Out of money it’s easy to fall victim to a financial scam on the Dark Web because of the anonymous and secretive nature of the communications and activities that take place there.
Damages from cybercrime were estimated to exceed $4.2 billion in 2020. Because only a minority of cyberattacks and events are ever recorded, the true scope of the damage is likely substantially higher.
Sources
- Finklea, K. (2017). “Dark Web” Congressional Research Service https://a51.nl/sites/default/files/pdf/R44101%20(1).pdf
- Berghel, H. (2017). “Which Is More Dangerous— the Dark Web or the Deep State?” THE IEEE COMPUTER SOCIETY http://www.berghel.net/col-edit/out-of-band/july-17/oob_7-17.pdf
- McCallister, E. (2010). “Guide to protecting the confidentiality of personally identifiable information.” Diane Publishing https://books.google.com.pk/books?hl=en&lr=&id=tlTrkXB-f3cC&oi=fnd&pg=PR6&dq=personally+identifiable+information&ots=Sk6WvIFgnb&sig=Vau-q76WAYC9xS_-2otd6yOPUY8&redir_esc=y#v=onepage&q=personally%20identifiable%20information&f=false
- Weimann, G. (2016). “Going dark: Terrorism on the dark web.” Studies in Conflict & Terrorism https://www.tandfonline.com/doi/abs/10.1080/1057610X.2015.1119546
- Liggett, R., Lee, J. R., Roddy, A. L., & Wallin, M. A. (2020). “The dark web as a platform for crime: An exploration of illicit drug, firearm, CSAM, and cybercrime markets. The Palgrave handbook of international cybercrime and cyberdeviance” SpringerLink https://link.springer.com/referenceworkentry/10.1007/978-3-319-78440-3_17















